An
Internet Protocol address (
IP address) is a numerical label assigned to each device (e.g., computer, printer) participating in a
computer network that uses the
Internet Protocol for communication. An IP address serves two principal functions: host or network interface
identification and location
addressing. Its role has been characterized as follows: "
A name indicates what we seek. An address indicates where it is. A route indicates how to get there."
The designers of the Internet Protocol defined an IP address as a
32-bit number and this system, known as
Internet Protocol Version 4 (IPv4), is still in use today. However, due to the enormous growth of the
Internet and the predicted
depletion of available addresses, a new addressing system (
IPv6), using 128 bits for the address, was developed in 1995,standardized as
RFC 2460 in 1998, and is being deployed worldwide since the mid-2000s.
IP addresses are
binary numbers, but they are usually stored in text files and displayed in
human-readable notations, such as 172.16.254.1 (for
IPv4), and 2001:db8:0:1234:0:567:8:1 (for
IPv6).
IP versions
Two versions of the Internet Protocol (IP) are in use: IP Version 4 and IP Version 6. Each version defines an IP address differently. Because of its prevalence, the generic term
IP address typically still refers to the addresses defined by
IPv4. The gap in version sequence between IPv4 and IPv6 resulted from the assignment of number 5 to the experimental
Internet Stream Protocol in 1979, which however was never referred to as IPv5.
IP version 4 addresses
In IPv4 an address consists of 32
bits which limits the
address space to
4294967296 (2
32) possible unique addresses. IPv4 reserves some addresses for special purposes such as
private networks (~18 million addresses) or
multicast addresses (~270 million addresses).
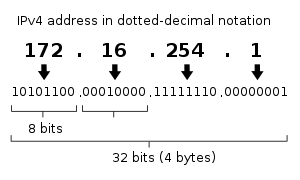
IPv4 addresses are canonically represented in
dot-decimal notation, which consists of four decimal numbers, each ranging from 0 to 255, separated by dots, e.g., 172.16.254.1. Each part represents a group of 8 bits (octet) of the address. In some cases of technical writing, IPv4 addresses may be presented in various
hexadecimal,
octal, or
binary representations.
IPv4 subnetting
In the early stages of development of the Internet Protocol, network administrators interpreted an IP address in two parts: network number portion and host number portion. The highest order octet (most significant eight bits) in an address was designated as the
network number and the remaining bits were called the
rest field or
host identifier and were used for host numbering within a network.
This early method soon proved inadequate as additional networks developed that were independent of the existing networks already designated by a network number. In 1981, the Internet addressing specification was revised with the introduction of
classful network architecture.
Classful network design allowed for a larger number of individual network assignments and fine-grained
subnetwork design. The first three bits of the most significant octet of an IP address were defined as the
class of the address. Three classes (
A,
B, and
C) were defined for universal
unicast addressing. Depending on the class derived, the network identification was based on octet boundary segments of the entire address. Each class used successively additional octets in the network identifier, thus reducing the possible number of hosts in the higher order classes (
B and
C). The following table gives an overview of this now obsolete system.
Historical classful network architecture
| Class | Leading
address bits | Range of
first octet | Network ID
format | Host ID
format | Number of networks | Number of addresses |
|---|
| A | 0 | 0 - 127 | a | b.c.d | 27 = 128 | 224 = 16777216 |
|---|
| B | 10 | 128 - 191 | a.b | c.d | 214 = 16384 | 216 = 65536 |
|---|
| C | 110 | 192 - 223 | a.b.c | d | 221 = 2097152 | 28 = 256 |
|---|
Classful network design served its purpose in the startup stage of the Internet, but it lacked
scalability in the face of the rapid expansion of the network in the 1990s. The class system of the address space was replaced with
Classless Inter-Domain Routing (CIDR) in 1993. CIDR is based on variable-length subnet masking (VLSM) to allow allocation and routing based on arbitrary-length prefixes.
Today, remnants of classful network concepts function only in a limited scope as the default configuration parameters of some network software and hardware components (e.g. netmask), and in the technical jargon used in network administrators' discussions.
IPv4 private addresses
Early network design, when global end-to-end connectivity was envisioned for communications with all Internet hosts, intended that IP addresses be uniquely assigned to a particular computer or device. However, it was found that this was not always necessary as
private networks developed and public address space needed to be conserved.
Computers not connected to the Internet, such as factory machines that communicate only with each other via TCP/IP, need not have globally unique IP addresses. Three ranges of IPv4 addresses for private networks were reserved in
RFC 1918. These addresses are not routed on the Internet and thus their use need not be coordinated with an IP address registry.
IPv6 private addresses
Just as IPv4 reserves addresses for private or internal networks, blocks of addresses are set aside in IPv6 for private addresses. In IPv6, these are referred to as
unique local addresses (ULA).
RFC 4193 sets aside the routing prefix fc00::/7 for this block which is divided into two /8 blocks with different implied policies The addresses include a 40-bit pseudorandom number that minimizes the risk of address collisions if sites merge or packets are misrouted.
Early designs used a different block for this purpose (fec0::), dubbed site-local addresses.However, the definition of what constituted
sites remained unclear and the poorly defined addressing policy created ambiguities for routing. This address range specification was abandoned and must not be used in new systems.
Addresses starting with fe80:, called
link-local addresses, are assigned to interfaces for communication on the link only. The addresses are automatically generated by the operating system for each network interface. This provides instant and automatic network connectivity for any IPv6 host and means that if several hosts connect to a common hub or switch, they have a communication path via their link-local IPv6 address. This feature is used in the lower layers of IPv6 network administration (e.g.
Neighbor Discovery Protocol).
None of the private address prefixes may be routed on the public Internet.
IP subnetworks
IP networks may be divided into
subnetworks in both IPv4 and IPv6. For this purpose, an IP address is logically recognized as consisting of two parts: the
network prefix and the
host identifier, or
interface identifier (IPv6). The
subnet mask or the
CIDR prefix determines how the IP address is divided into network and host parts.
The term
subnet mask is only used within IPv4. Both IP versions however use the
Classless Inter-Domain Routing (CIDR) concept and notation. In this, the IP address is followed by a slash and the number (in decimal) of bits used for the network part, also called the
routing prefix. For example, an IPv4 address and its subnet mask may be 192.0.2.1 and 255.255.255.0, respectively. The
CIDR notation for the same IP address and subnet is 192.0.2.1/24, because the first 24 bits of the IP address indicate the network and subnet.
Uses of dynamic addressing
Dynamic IP addresses are most frequently assigned on LANs and broadband networks by
Dynamic Host Configuration Protocol (DHCP) servers. They are used because it avoids the administrative burden of assigning specific static addresses to each device on a network. It also allows many devices to share limited address space on a network if only some of them will be online at a particular time. In most current desktop operating systems, dynamic IP configuration is enabled by default so that a user does not need to manually enter any settings to connect to a network with a DHCP server. DHCP is not the only technology used to assign dynamic IP addresses. Dialup and some broadband networks use dynamic address features of the
Point-to-Point Protocol.
Sticky dynamic IP address
A
sticky dynamic IP address is an informal term used by cable and DSL Internet access subscribers to describe a dynamically assigned IP address that seldom changes. The addresses are usually assigned with the DHCP protocol. Since the modems are usually powered-on for extended periods of time, the
address leases are usually set to long periods and simply renewed upon expiration. If a modem is turned off and powered up again before the next expiration of the address lease, it will most likely receive the same IP address.
Public addresses
A
public IP address in common synonymous with a, globally routable unicast IP address.
Both IPv4 and IPv6 define address ranges that are reserved for
private networks and
link-local addressing. The term public IP address often used exclude these types of addresses.